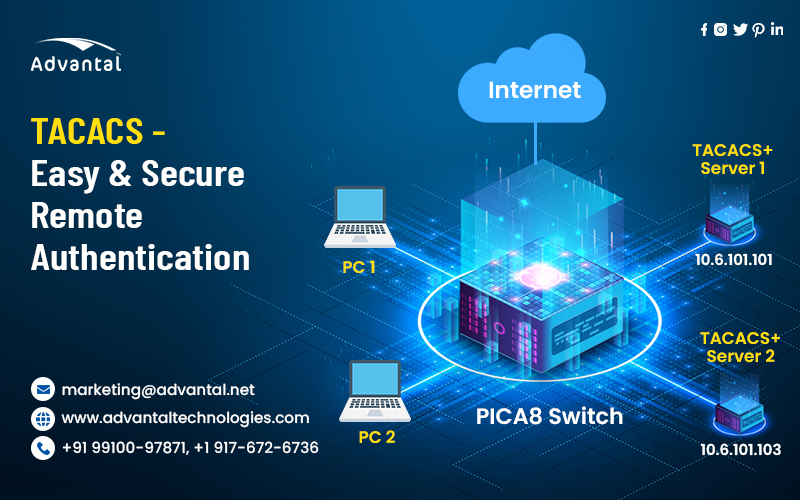
TACACS, which stands for Terminal Access Controller Access Control System (or some similar variation), was a proprietary protocol designed by Cisco in the early 1990s for remote user authentication and authorization.
Today, TACACS is still used to authenticate remote users who need access to network devices—including routers, switches, network access servers (NAS), firewalls, and other devices.
This article will explore what TACACS is and why it exists. We’ll also explain how it works and whether organizations still use it today.
Remote Authentication
Authentication is the process of verifying a user’s identity. The authentication process helps ensure that only authorized users can access your network, and it is usually part of a larger authentication system called AAA (Authentication, Authorization, and Accounting). Authentication involves three parties:
- The supplicant – client requesting access to resources on an Access Control Server (ACS).
- A RADIUS server – receives the request from the client and forwards it to an ACS. In this case, an ACS acts as a RADIUS server because it supports RADIUS protocol.
- An Access Control Server – provides authorization services for users trying to gain access to resources on an 802.1x-enabled device or switch port.
What is TACACS, and What Does it Do?
TACACS is a remote authentication protocol that provides centralized access control to resources. It allows administrators to authenticate users and authorize them for various services on a device.
TACACS provides authentication and authorization services for remote access to network devices such as routers, switches, or firewalls.
How Does TACACS Work?
Here is how the Terminal Access Controller Access Control System works:
- When a device needs to be authenticated, it sends an authentication request to the central server.
- The server processes the request and sends back a response with all the necessary information for authentication.
- The device receives this response and then forwards it to the server as confirmation that it has been authenticated successfully. It is known as two-way communication between the device and the central server.
- The authentication process ends when an authentication success or failure message is sent from the central server to your device, which then displays these messages on its screen, so you know whether or not your TACACS session was successful.
Is TACACS Secure?
Organizations use TACACS as an additional security measure in addition to the password system. TACACS-user authentication allows you to ensure that only authorized users can connect to your device and get access to it remotely.
TACACS is a secure protocol. It uses TCP port 49 and UDP port 49, which can only be transmitted over a trusted network. It prevents anyone from intercepting the connection or sniffing the passwords sent between the server and the client. In addition, the authentication information is encrypted before it travels across any untrusted networks.
Is TACACS Still Used Today?
You may be wondering if TACACS is still used today. The answer is yes. TACACS servers are still in use by many companies, and they’re used in a wide range of industries. For example, some companies continue to use TACACS because they have legacy products that require it. Others choose it because they want to maintain compatibility with other systems (such as Active Directory) which use the same technology.
The main reason people continue to use TACACS authentication today is that it’s so flexible and secure. TACACS can implement through both network devices or user accounts depending on what your organization needs at the time of implementation; this gives you more control over who has access to certain parts of your system than other authentication methods.
Conclusion
To summarize, TACACS authentication is a type of AAA (Authentication, Authorization, and Accounting) protocol used to control user access to network services. It uses TCP port 49 instead of UDP. Because it’s centralized and allows for better encryption than RADIUS, this protocol is more secure than its alternatives. In addition, these protocols are not mutually exclusive and can be used together to ensure optimal security on your network.